Revolutionizing IAM:
Mastering Identity Orchestration
A unique drag-and-drop framework for mapping the user journeys during all phases of the identity lifecycle, including provisioning, authentication, and authorization. Monokee enables enterprise teams to build user journeys with a codeless approach, drastically reducing the integration complexity and time.
AN INTRODUCTION TO V.I.O.
How the Visual Identity Orchestrator of Monokee works
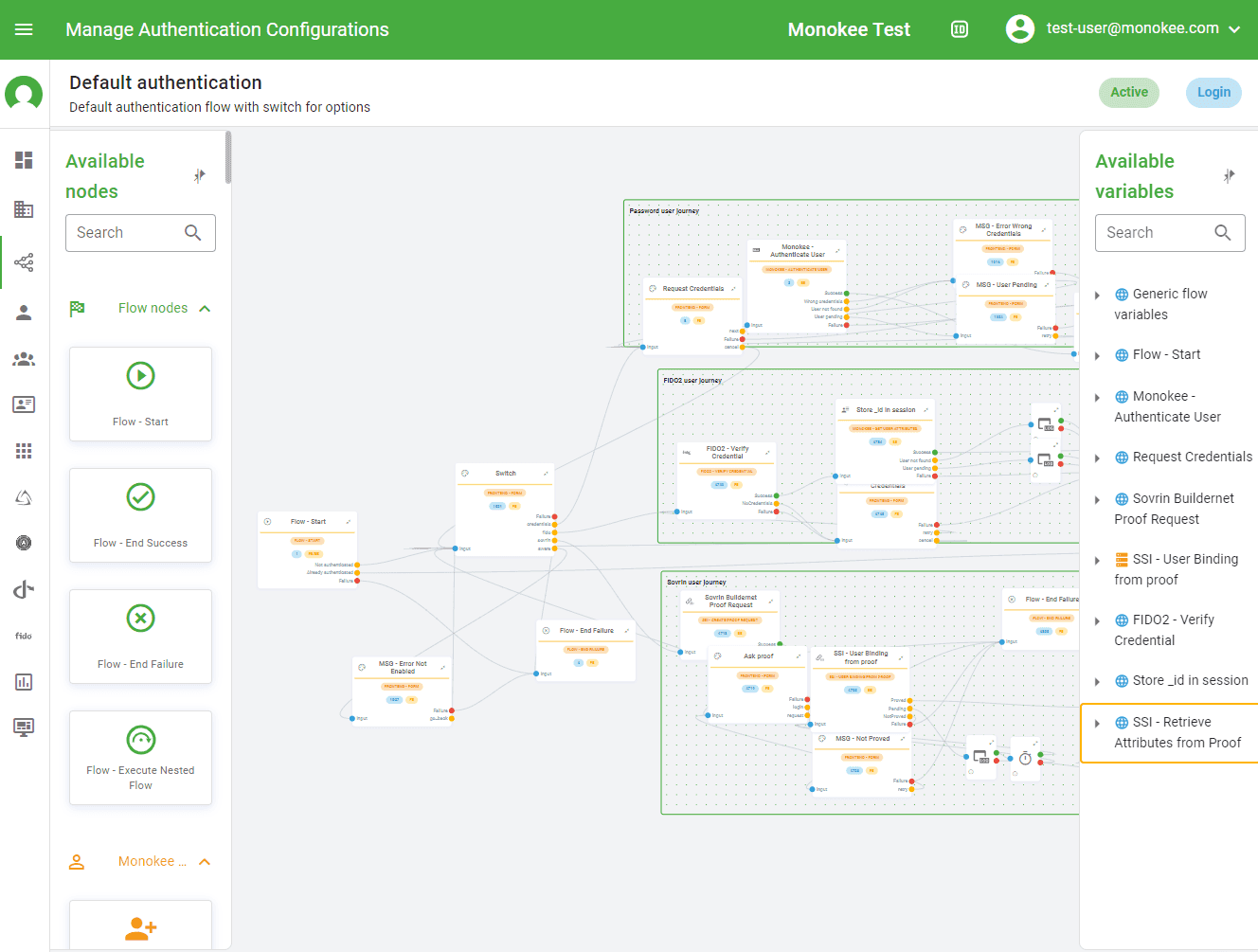
Step One
Draw your user journey
Begin by mapping out your user's journey using our intuitive block diagram tool. Select from predefined components in our palette to chart each step of the user experience, clearly visualizing every interaction point within the system. This process allows you to identify and optimize every phase of the user journey, ensuring a smooth and consistent experience.
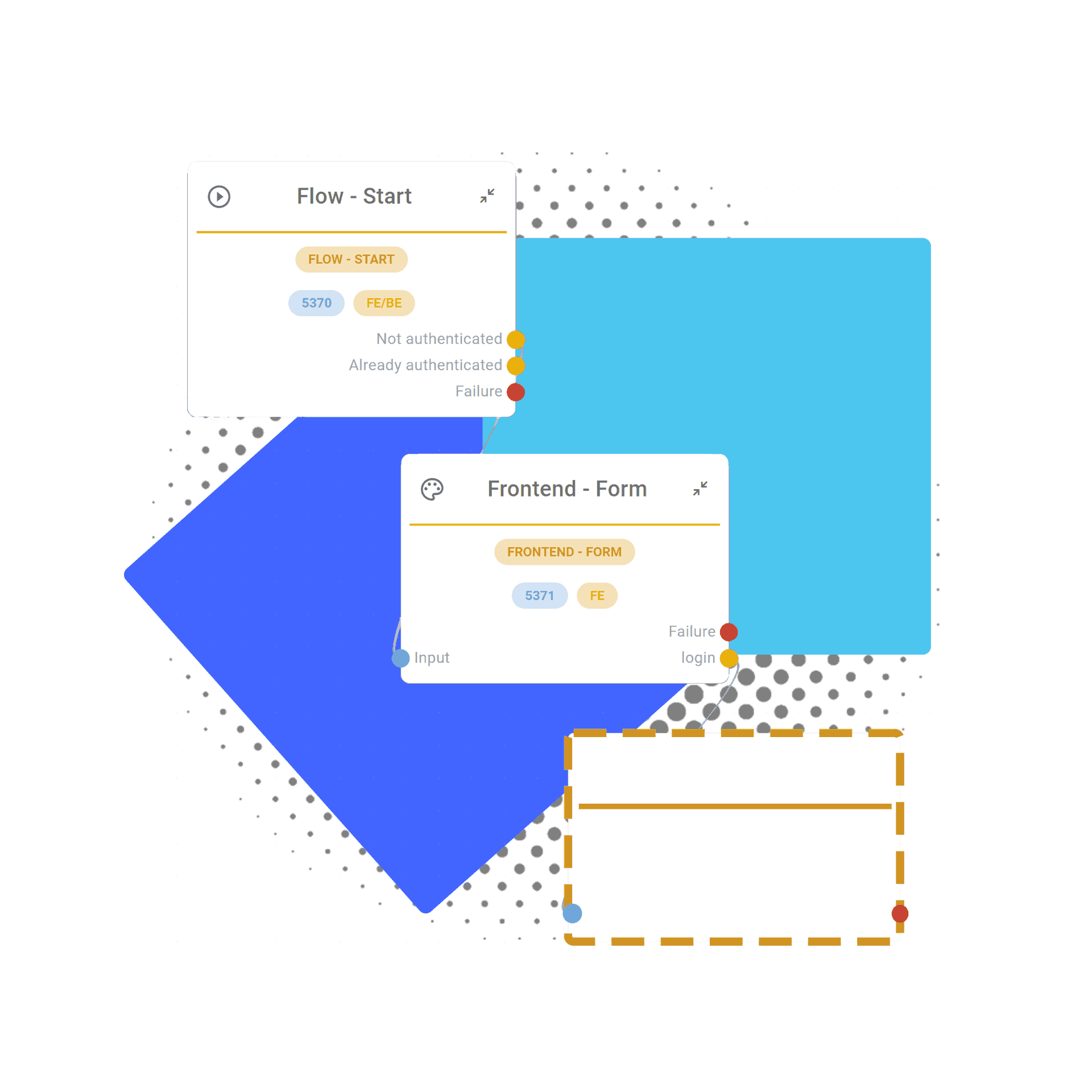
Step Two
Integrate with third-party tools
Enhance the security and efficiency of your user access flow by seamlessly integrating with cutting-edge third-party systems. Our platform enables you to incorporate Multi-Factor Authentication (MFA) for enhanced security, risk analysis tools for smarter decision-making, and just-in-time provisioning for streamlined access management. Simplify complex integrations and empower your system with robust, sophisticated solutions that are just a few clicks away.
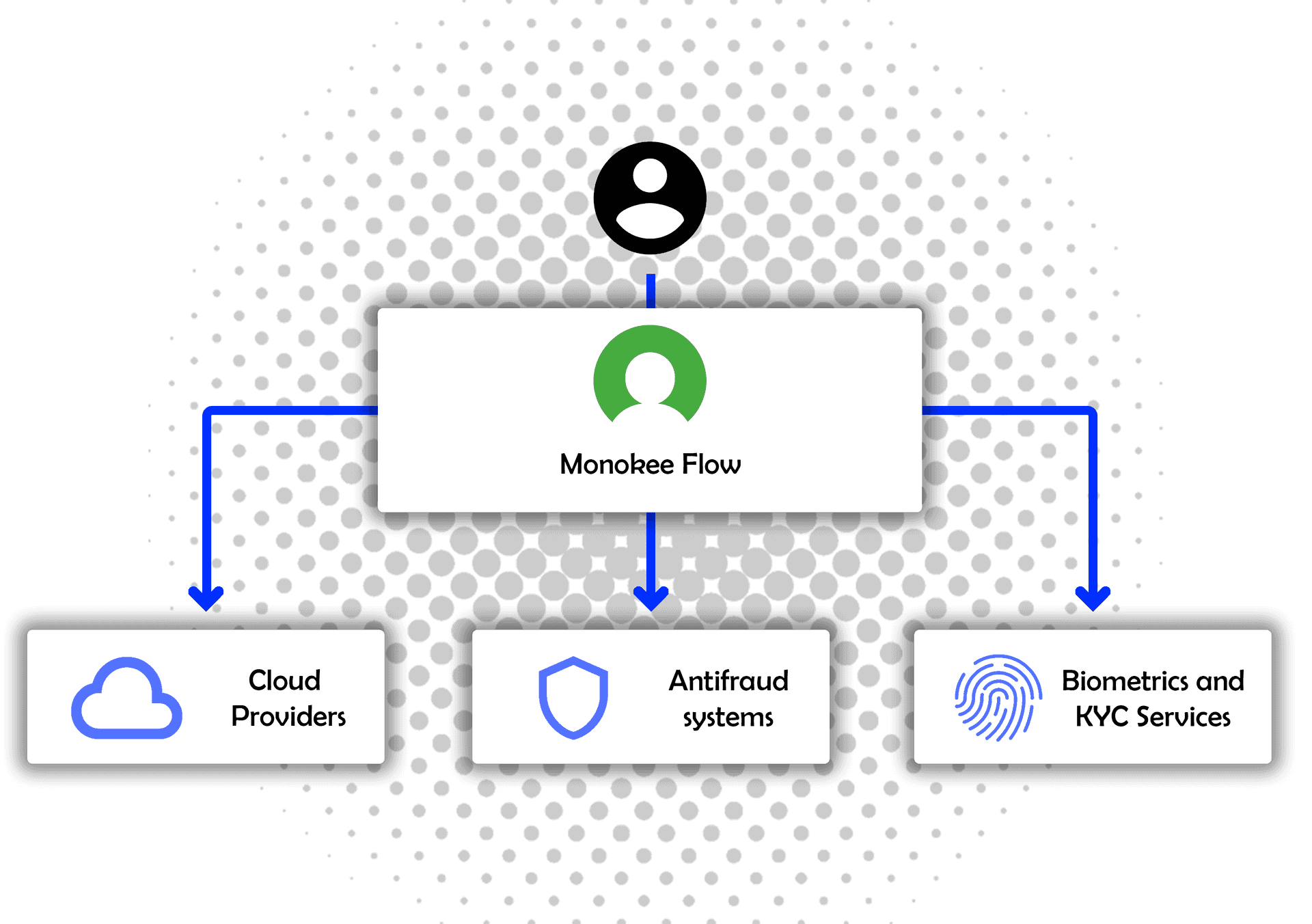
Step Three
Multi-Domain Deployment Made Easy
Expand your reach effortlessly with our platform's capability to deploy user access flows across multiple domains. Tailor your user journey for different segments or departments within your organization, ensuring a consistent yet customized experience. Our tool simplifies the complexity of multi-domain deployment, allowing you to manage diverse user requirements with ease and precision. Embrace the power of flexibility and scalability, ensuring your access flows are perfectly aligned with your organizational structure and goals.
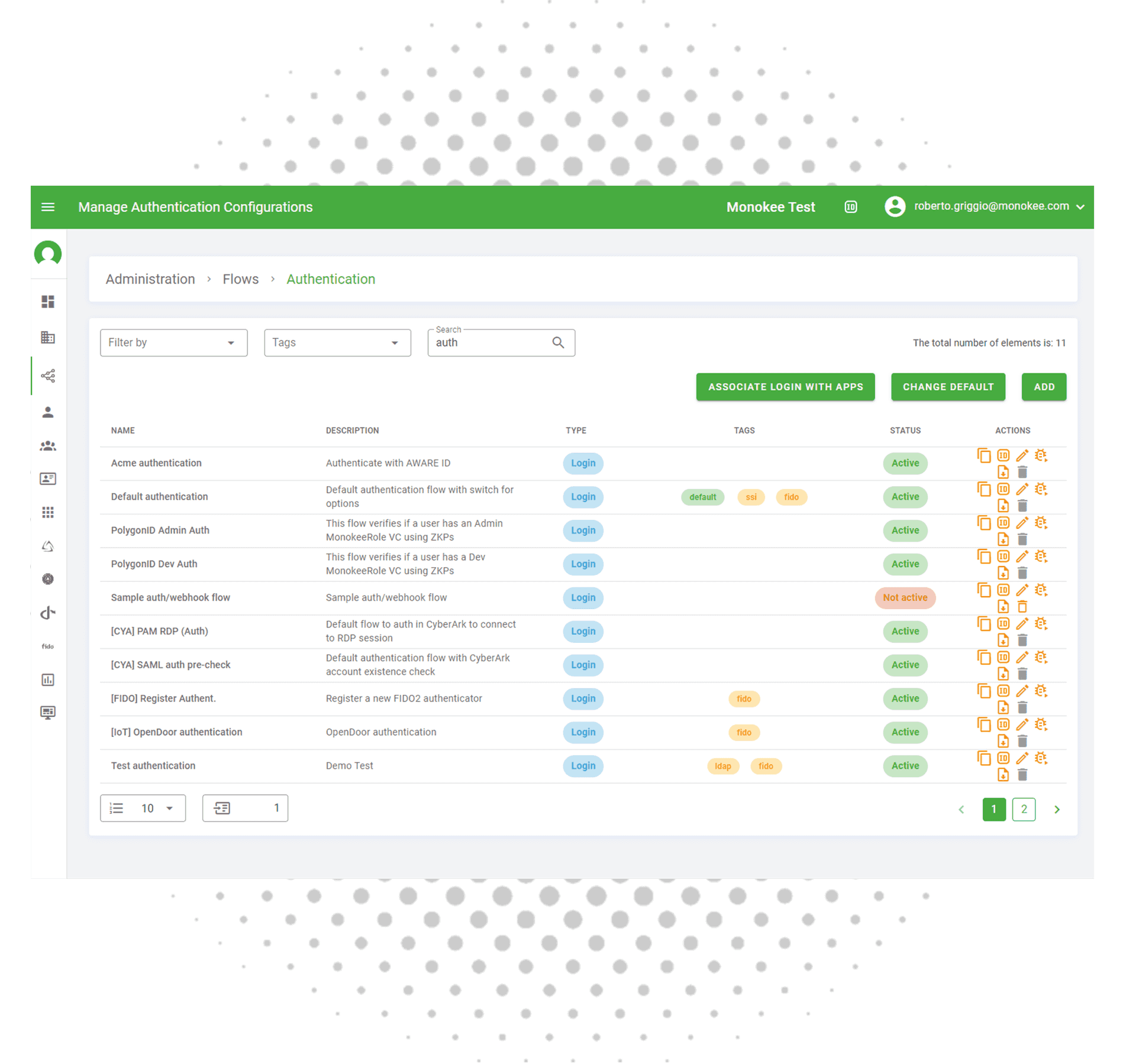
Step Four
Secure Your Applications with Custom Flows
Fortify your applications by integrating them with specialized access flows. Our platform enables you to design and implement robust security protocols tailored to each application's unique needs. Whether it’s ensuring secure logins, managing user permissions, or monitoring access patterns, our solution provides you with the tools to safeguard your applications effectively. Enhance your application security with custom, user-centric access flows that are both secure and seamless, thereby striking the perfect balance between protection and usability.